| Tutorial >> Router Plugins |
|
This example illustrates the use of a router plugin to mitigate the effects of a SYN flood attack. The demonstration uses many of the novel features of the ONL testbed: 1) A sophisticated router plugin; 2) Real-time displays; and 3) Packet filters. In a SYN flood attack, a malicious sender attempts to block new TCP connections at a target by sending SYN packets to begin the process of creating connections that it never intends to complete. Although host-based techniques for dealing with SYN flood attacks have now been widely adopted, this nonetheless provides a useful illustration of how new capabilities can be added to an NSP using software plugins.
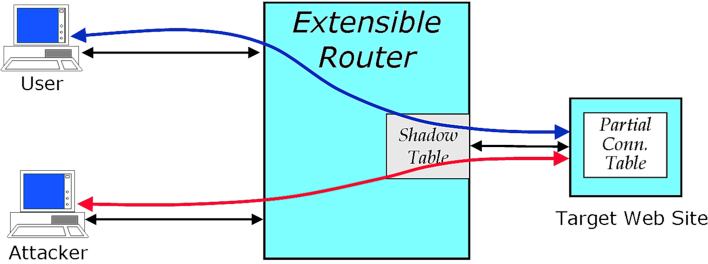
The essential elements of the experiment are shown in Fig. 1. A browser repeatedly makes legitimate TCP connections to a target Web site to send HTTP image requests. Concurrently, an attacker sends a flood of spoofed SYN packets that each begins but never completes the process of creating a TCP connection. Eventually, the partial connections at the target Web site exhaust the site's partial connection table blocking new connections from legitimate users.
The NSP's plugin facility can be used to mitigate the effects of this type of DoS attack. TCP connection packets are diverted to a plugin at the egress port leading to the target web site. The plugin monitors partial TCP connections, records these connections in its shadow table, and clears those that don't complete in time. In order to monitor the connection and termination phases of TCP connections, two GM filters are installed which divert these packets through the plugin. If the three-way connect handshake succeeds, the plugin installs an EM filter to allow the web server's response packets to pass through the port without plugin processing. Since the reply traffic accounts for the bulk of the bandwidth usage at the web site, this keeps the amount of traffic that must be handled by the SPC relatively modest. However, when the plugin recognizes that a partial connection (from the attacker) has timed out, it sends a ReSeT packet to the server to release the resources consumed by the incomplete connection and deletes the entry from its shadow table. This ReSeT packet carries the source IP address that was used by the SYN packet that initiated the connection, making the attack mitigation mechanism completely transparent to the target web site.
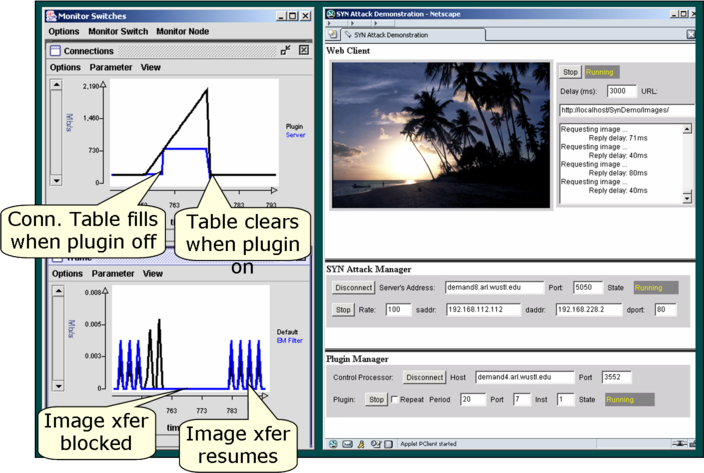
Fig. 2 shows several displays used to
demonstrate this new feature.
On the right is a browser window with three
Java applet panels.
The applet in the top panel plays the role of a Web client
sending HTTP image requests at a specified rate (every 3
seconds in the example) and displaying
the reply images and response times.
When an attack is successful, the image sequence freezes
instead of displaying a new image every 3 seconds.
The middle panel is used to control the attack daemon,
and the bottom panel is used to
enable/disable the plugin.
The displays on the left show monitored data.
In both cases, the plugin has been disabled
during the middle of the time interval shown.
The bottom display shows the image traffic volume.
During a successful attack when the plugin is disabled,
image transfers stop shortly after the plugin has been disabled.
The top display shows the number of incomplete connections as
viewed by the Web server and the plugin.
It shows that the Web server's
connection table tops out (lower curve) while the plugin
continues to see additional attacker packets.
Revised: Wed, July 12, 2006
| Tutorial >> Router Plugins |
|